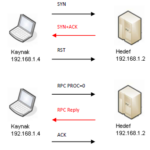
RPC Scan, hedef makina üzerinde koşan RPC uygulamalarını keşfeder. Başka bir tarama türü ile açık portlar keşfedildikten sonra,RPC Scan hedef makinanın açık portlarına RPC null göndererek, eğer çalışan bir RPC uygulaması varsa, RPC uygulamasını harekete geçirir.RPC Scan, Version Detection Scan işlemi esnasında otomatik olarak çalıştırılır.
Bu taramayı gerçekleştirmek için aşağıdaki komut kullanılmalıdır :
nmap -sR -v [Hedef_IP]
nmap -sR -v 192.168.1.2
at 2010-08-01 18:53 EEST
Initiating ARP Ping Scan at 18:53
Scanning 192.168.1.2 [1 port]
Completed ARP Ping Scan at 18:53, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:53
Completed Parallel DNS resolution of 1 host. at 18:53, 0.02s elapsed
Initiating SYN Stealth Scan at 18:53
Scanning 192.168.1.2 [1000 ports]
Discovered open port 111/tcp on 192.168.1.2
Discovered open port 80/tcp on 192.168.1.2
Discovered open port 53/tcp on 192.168.1.2
Discovered open port 22/tcp on 192.168.1.2
Discovered open port 2049/tcp on 192.168.1.2
Completed SYN Stealth Scan at 18:53, 2.28s elapsed (1000 total ports)
Initiating RPCGrind Scan against 192.168.1.2 at 18:53
Completed RPCGrind Scan against 192.168.1.2 at 18:53, 0.36s elapsed (5 ports)
Nmap scan report for 192.168.1.2
Host is up (0.0012s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open unknown
53/tcp open unknown
80/tcp open unknown
111/tcp open unknown
2049/tcp open nfs (nfs V2-4) 2-4 (rpc #100003)
MAC Address: 00:0C:29:D7:D3:65 (VMware)
Read data files from: /usr/local/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2.84 seconds
Raw packets sent: 1098 (48.296KB) | Rcvd: 1001 (40.048KB)