 Occasionally, i do security tests on my web site. Above all i keen on security as you know. I continuously follow lots of security forums or look alikes. I spot security checks on my web site, and if there is an issue, i interfere to incident. Again, while i was testing, there occured a XSS vulnerability.
Occasionally, i do security tests on my web site. Above all i keen on security as you know. I continuously follow lots of security forums or look alikes. I spot security checks on my web site, and if there is an issue, i interfere to incident. Again, while i was testing, there occured a XSS vulnerability.
Normally, there is no vulnerability like this on WordPress. Problem occurs because of some kind of codes which are added on WordPress for SEO. It is recommended that, in addition to add-ons which improve SEO system on WordPress, additional codes should be advised to people to use. But one of the most famous additional codes could expose a vulnerability on your wordpress system.
Followings are the codes which expose XSS vulnerability:
<meta name="description" content="<?php if (is_home() ) {?><?php bloginfo('description');} elseif ( is_single() ) { ?><?php wp_title(''); ?> , <?php $cat = get_the_category(); $cat = $cat[0]; echo $cat->cat_name; ?> , <?php bloginfo('description'); } elseif ( is_page() ) { ?><?php wp_title(''); ?> , <?php bloginfo('description'); } elseif ( is_category() ) { ?> <?php single_cat_title('');?> , <?php bloginfo('description'); } elseif ( is_archive() ) { ?><?php wp_title(''); ?> , <?php bloginfo('description'); } elseif ( is_search() ) { ?> <?php echo $s; ?> , <?php bloginfo('description'); } elseif (is_tag()) {$tagTitle = preg_replace('/-/' , ' ' , $tag); echo ucwords($tagTitle); ?> , <?php $cat = get_the_category(); $cat = $cat[0]; echo $cat->cat_name; ?> , <?php bloginfo('description'); } else { ?><?php wp_title(''); ?> , <?php bloginfo('description'); }?>" />
The code above is SEO code which was prepared for WordPress. It is signified on many kinds of SEO forums, forums and web sites that if you add the code above to header.php file on your theme, it will be beneficial for google-seo compatibility. It is true,through the code above your “meta description” tag acquires functionality and you can get better results on google side but there is a forgotten structure in this code.
If you look at the search result below, you will recognize thousands of people use this code:
http://www.google.com
Search function of WordPress “/s=search” was added to this code. As you can the coding above, through function, a description tag which was supplied to be formed by system for publishing search words. But this function tangles you.
XSS Security Vulnerability,
It would tangle you that if there is SEO code which comes within your theme was added to your WordPress, or read some articles from R10.net or alike and then use this code, or you hired anybody for doing SEO. Unfortunately, through this code, a malicious person can attack your blog and hack your system.
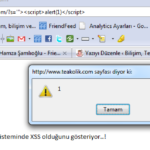
http://www.TEAkolik.com/?s='"><script>alert(1)</script>
As such you can see if there is a XSS vulnerability on your wordpres system. Whether there comes a popup screen, then there is a security vulnerability.
Normally there is not coding such as this;
There is no coding in WordPress standarts. But functions were combined by SEO maker Guys and then a new type of code is exposed. Thanks to this, you can add to your header.php file and use it. But risk is so high. Especially, some of the people mentioned to add this code to your theme in lots of forums. Currently, many of people are using this code at their blogs, and it comes within theme standartly.
As a brief, it incurs a risk for you!
What should be done?
I summarize and tell shortly. Teach hacking is not my intention just provide your security. An attacker can do lots of things if you have this code in your system. I am passing this subject and not telling what can be done. Because there may be some of people who wants to use it maliciously. I suggest you that alter the code which is in your system like i mentioned below urgently.
Solution,
You should eliminate search parameters which expose XSS vulnerability from code to get over this.
Clean codes ( XSS eliminated);
<meta name="description" content="<?php if (is_home() ) {?><?php bloginfo('description');} elseif ( is_single() ) { ?><?php wp_title(''); ?> , <?php $cat = get_the_category(); $cat = $cat[0]; echo $cat->cat_name; ?> , <?php bloginfo('description'); } elseif ( is_page() ) { ?><?php wp_title(''); ?> , <?php bloginfo('description'); } elseif ( is_category() ) { ?><?php single_cat_title('');?> , <?php bloginfo('description'); } elseif ( is_archive() ) { ?><?php wp_title(''); ?> , <?php bloginfo('description'); } elseif (is_tag()) {$tagTitle = preg_replace('/-/' , ' ' , $tag); echo ucwords($tagTitle); ?> , <?php $cat = get_the_category(); $cat = $cat[0]; echo $cat->cat_name; ?> , <?php bloginfo('description'); } else { ?><?php wp_title(''); ?> , <?php bloginfo('description'); }?>" />
There will no security risk, whether it is used like this. Now, you should use clean codes if you have the code which expose XSS from header.php.
http://www.TEAkolik.com/?s='"><script>alert(1)</script>
If you try the url above, you will recognize there is no XSS. The web site work normally, if you use clean codes.
Please use the codes to provide security, i will be no responsible because of the problems which may occur in your system. Please ensure you control your system. If you may use this article, i will ask you that add TEAkolik.com link.
Thank You.
Already more power to your elbow!

Güzel çevirmişim be :):)
aga bu nedir 😀
@Kr4L
bir önceki yazının ingilizce versiyonu 😀
very good!
http://www.teakolik.com – оказывается ещё и полезный )
Hack again?!